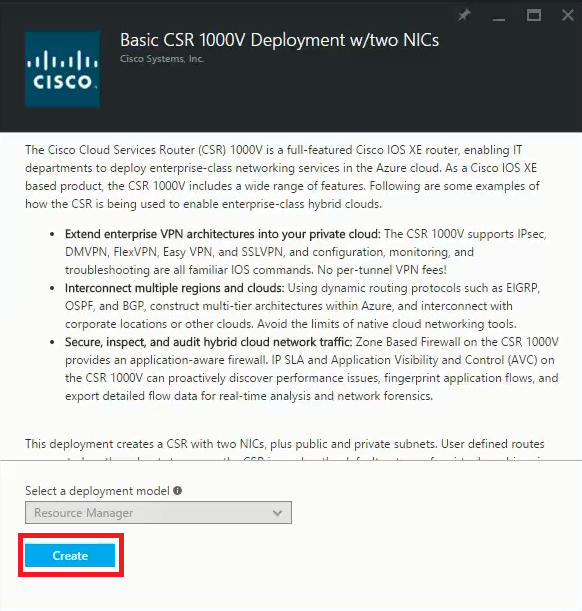
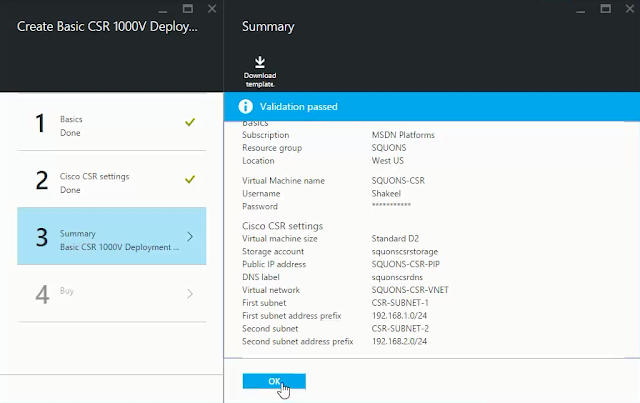
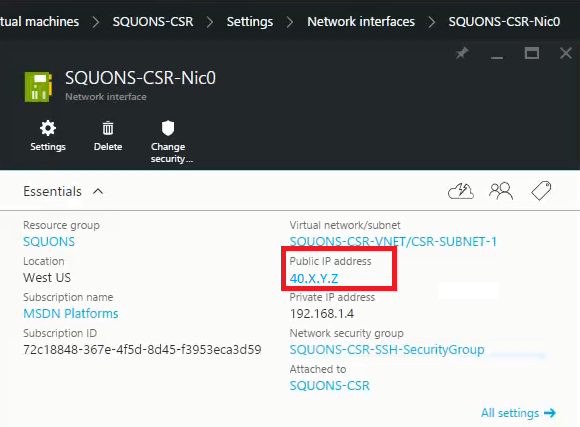
This blog will guide you step by step to migrate VM from Amazon AWS to Microsoft Azure using ASR (Azure Site Recovery). ASR is a Business Continuity and Disaster Recovery (BCDR) solution from Microsoft which is used to protect company’s on-premise physical/virtual machine by orchestrating the replication/failover process to Azure or secondary on-premise datacenter.
Entire migration process comprises of 4 components:
1.
Configuration Server: It coordinates and communicates between Master, Process and Protected Machine and sets up recovery & replication in Azure when failover occurs.
2.
Master Server: It receives and retain replicated data from Protected Machine using attached VHD’s created on BLOB storage.
3.
Process Server: It receives replication data from Protected machine and optimizes data by caching, compressing & encrypting before sending to Master. It also perform automatic discovery of VM and handles push installation of Mobility Service.
4.
Protected Machine: It is the machine which can be physical or virtual on Vmware ESXi, Microsoft Hyper-V and Amazon AWS that is to be protected on Azure.
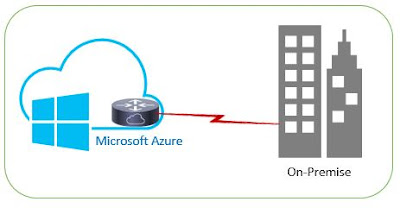
Following picture depicts architectural diagram which is considered for migrating VM from Amazon AWS to Microsoft Azure:
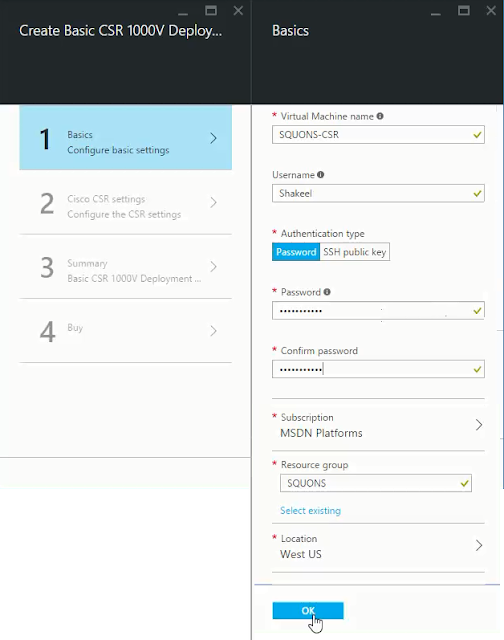
To begin with configuring above mentioned components, first we need to configure Site Recovery Vault.
After creating the Site Recovery Vault click on your Vault name.
It will prompt one window to define your purpose of deploying Site Recovery Vault. Define accordingly and click Ok.
Now let’s begin with configuring components one by one.
I. Configuring Configuration Server
1.
On Quick start up page click on Deploy Configuration Server.
2.
Fill the details of the Configuration Server and click Ok.
3.
It will take some time to deploy Configuration Server as you can see in Job.
4.
It automatically creates storage, cloud service, Endpoints and VM of Size Standard A3 with reserved ip configured.
5.
Take RDP of Configuration Server VM & you will observe one setup file on desktop which will execute automatically and pops up installer window.
Click Next.
6.
Accept Agreement.
7.
Enter Password for MySQL which will be installed automatically ahead in the step.
8.
Select your current Internet Setting.
9.
Select language for error message to be shown in portal.
10.
Now it will ask for Azure Site Recovery vault registration key which is available on startup page. Download and copy paste the vault credential key on Configuration Server. Click Install.
11.
It will take some time to install and click Finish.
12.
One window will open after installation displaying Configuration Server Connection Passphrase, copy and paste it somewhere as it will be used later while establishing connection with Master and Process Server.
13.
Next it will display a window which will ask to enter credential that will be used for logging in into Physical/Virtual Machine & deploy Mobility Service. Click Add Account.
14.
Enter credentials and click Ok.
II. Configuring Master Server
1.
On Quick start up page click on Deploy Master Target Server.
2.
Fill the details of the Master Server and click Ok.
3.
It will take some time to deploy Master Server as you can see in Job.
4.
Master Server VM and endpoints details are as follows:
5.
Take the RDP of the server, there you will see Host Agent Config window will be displayed. Here you need to specify details of the Configuration Server and Passphrase. Click Ok to proceed.
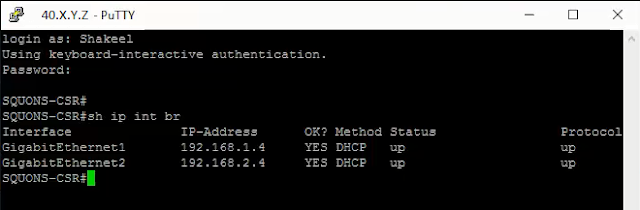
I have created 2 instance on Amazon AWS for Process Server and other as machine to be protected.
III. Configuring Process Server
1.
On Quick start up page click on Download and install Process Server.
You can download on your machine and then you can copy onto Process Server or copy the download link and download directly on Process Server.
2.
The folder consist of 2 application.
3.
First install Microsoft-ASR_CX_TP_8.4.0.0_Windows_GA_28Jul2015_release. Click Install.
4.
Click Finish after finishing the setup.
5.
Next install Microsoft-ASR_CX_8.4.0.0_Windows_GA_28Jul2015_release.
6.
Click Next.
7.
Select Process Server and click Next.
8.
Select No and click Next.
9.
Select NIC for Process Server and click Next.
10.
Enter details for Configuration Server i.e. its public ip address, endpoint https port and passphrase.
11.
Select the installation drive and click Install.
12.
It will display warning just ignore and click Yes.
13.
Click Finish and the Process Server will get rebooted.
14.
To check the Configuration Server setting and its status associated with Master and Process Server, goto ASR > Servers > Configuration Servers and click on configure Configuration Server
IV. Protecting Machine
1.
On Quick start up page click on Create Protection Group.
2.
Click on Create Protection Group.
3.
Mention the Group name, Select the Configuration Server and Target will be by default Microsoft Azure.
4.
Specify the Replication setting.
5.
Next we need to add the machine which is to be protected. To do so click on configured protection group.
6.
Click on Add Physical Machine.
7.
Provide the private ip address, friendly name and operating system of machine which is to be protected. Click Next.
8.
Now, Select the Process Server, Master Server and Storage Account. Click Next.
9.
Select the account which we have created on configuration Server which will be used to deploy Mobility Service on machine which is to be protected. Click Finish.
10.
It will take enough time to replicate from Amazon AWS to Microsoft Azure as depicted in Jobs.
After replicating and synchronizing completely go to protected machine and check the details of machine which will look like following snap:
Now to migrate the protected machine from Amazon AWS to Microsoft Azure click on Failover icon present on command bar.
It will prompt one window to confirm the unplanned failover and select the recovery point. Click Finish.
Now after sometime you can see your protected machine running under Virtual Machine on Microsoft Azure.